Cybercriminals continue to evolve, adapting faster than many organizations can respond. In 2025, cyber threats are becoming more advanced and deceptive, with tactics once considered fringe now moving mainstream. The landscape of cyber threats 2025 shows attackers targeting not just systems—but also user behavior, overlooked tools, and artificial intelligence.
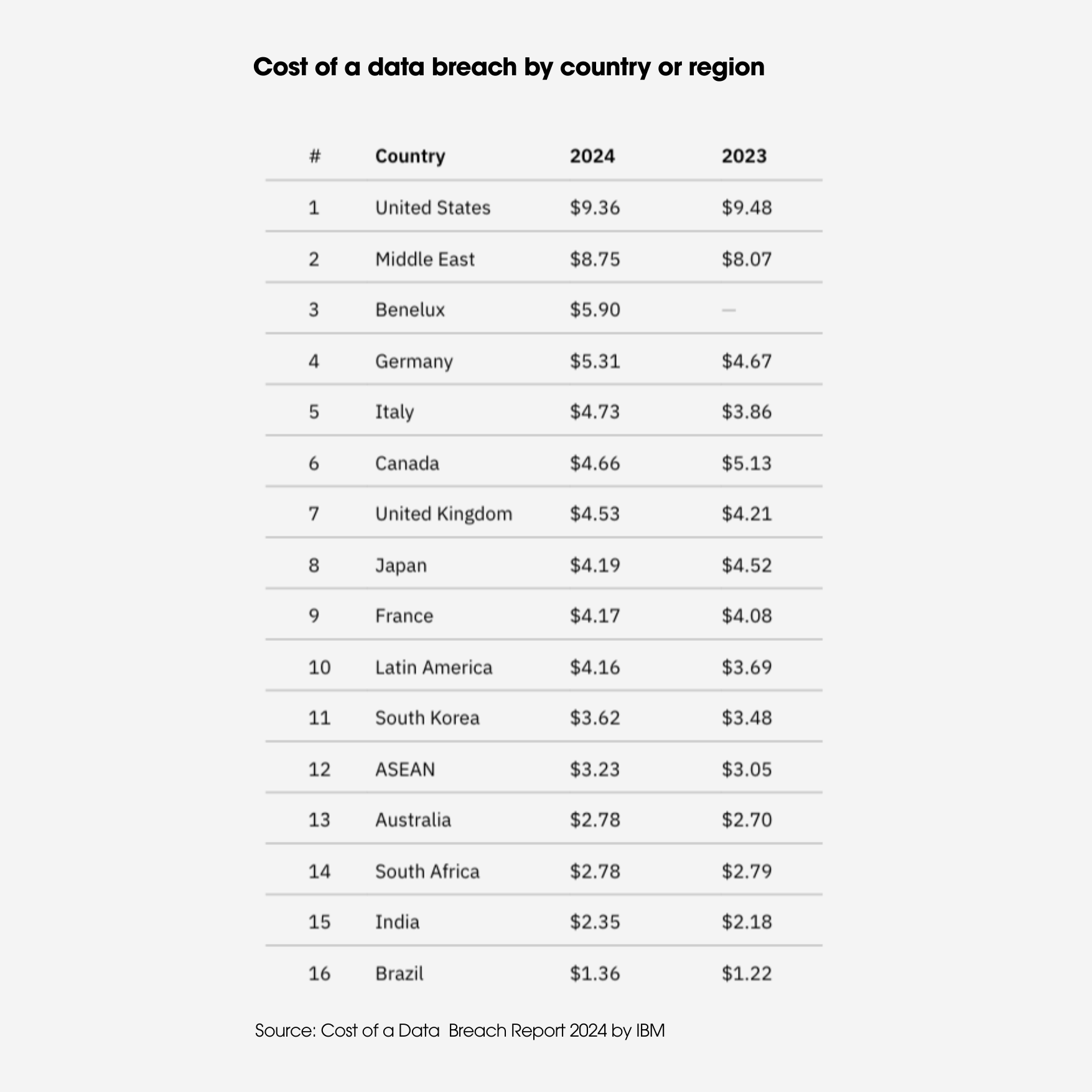
In 2020, Cybersecurity Ventures predicted that global cybercrime costs would grow by 15 percent per year over the next five years, reaching $10.5 trillion USD annually by 2025. Over the years, we have seen how the cost of data breaches and the frequency of cyberattacks have increased globally. According to the Cost of a Data Breach 2024 report by IBM, the average cost of a breach in Canada was USD $4.66 million, and USD $9.36 million in the United States. These figures highlight the urgent need for organizations to look more closely at their cybersecurity posture and invest in proactive risk management.
Cyber threats blending into everyday digital tools
As organizations accelerate digital transformation, attackers are exploiting every layer of technology. One of the more silent but persistent threats this year comes from WordPress Must-Use Plugins (MU-plugins). These tools run automatically on websites and cannot be disabled through the admin interface. While designed for essential functionality, cybercriminals are now abusing this feature to hide malware. Researchers from Sucuri uncovered a rise in malicious PHP files embedded in the mu-plugins directory. These files redirect users, open backdoors, and inject spam—often remaining undetected by administrators.
In another example of deceptive tactics, attackers are turning CAPTCHA pages into delivery mechanisms. Research shows that over 100 car dealership websites were compromised through a supply-chain attack. Instead of showing vehicle videos, the sites displayed fake CAPTCHA screens. These prompts instructed users to press Windows + R, then CTRL + V, and Enter. This sequence ran malware silently copied to the clipboard, bypassing traditional security tools. The attack, known as a “ClickFix” technique, relied on social engineering rather than technical exploits.
Attackers are also exploiting convenience. The FBI recently warned of malware distributed via free file converters. These tools are widely used to convert PDFs, videos, and audio files. But many are compromised with malicious code. Instead of performing simple tasks, they install malware that steals email credentials, passwords, crypto wallet keys, and Social Security numbers. The FBI describes these campaigns as “rampant,” with incidents reported in multiple U.S. cities.
Meanwhile, phishing tactics have shifted beyond email. Cybercriminals are now weaponizing Android apps. In 2024, over 22,800 phishing apps were detected. These apps mimic trusted services like TikTok and Spotify. Once installed, they harvest login credentials and intercept SMS-based multifactor authentication codes. Some serve deceptive ads, redirecting users to credential-harvesting pages. As mobile device usage grows, attackers are increasingly targeting the apps users trust most. Reports show that the most frequently compromised data types in breaches are customer PII, intellectual property, and employee PII.

Even AI systems are not immune. In fact, the National Cyber Threat Assessment 2025–2026 warns that AI technologies are likely reducing barriers for malicious cyber activity while increasing its sophistication, scale, and accuracy. Cybercriminals are leveraging generative and predictive AI tools—including large language models (LLMs)—to support various aspects of their operations, from generating malicious content to analyzing large datasets. It is highly likely that technically proficient threat actors will continue to experiment with new ways to exploit AI tools, including automating segments of the cyberattack lifecycle to enhance efficiency.

Ransomware operations and AI exploits define cyber risks in 2025
Prompt injection has become a rising concern in 2025. This tactic embeds hidden instructions into documents using invisible Unicode characters. When AI tools interact with these files—such as scanning emails or PDFs—they may unknowingly execute the malicious commands. The user remains unaware, but the AI’s output is manipulated. As organizations integrate generative AI into workflows, the risk of silent manipulation becomes real.
At the core of this evolving landscape is ransomware-as-a-service (RaaS). Groups like VanHelsing, BlackLock, Lynx, and Medusa are redefining what ransomware operations look like.
VanHelsing offers affiliates 80 percent of all ransom proceeds, with payments reaching up to $500,000. It now targets Windows, Linux, ARM, and VMware ESXi systems. BlackLock, originally called El Dorado, rebranded and launched 48 attacks in early 2025, primarily hitting real estate, manufacturing and construction firms.
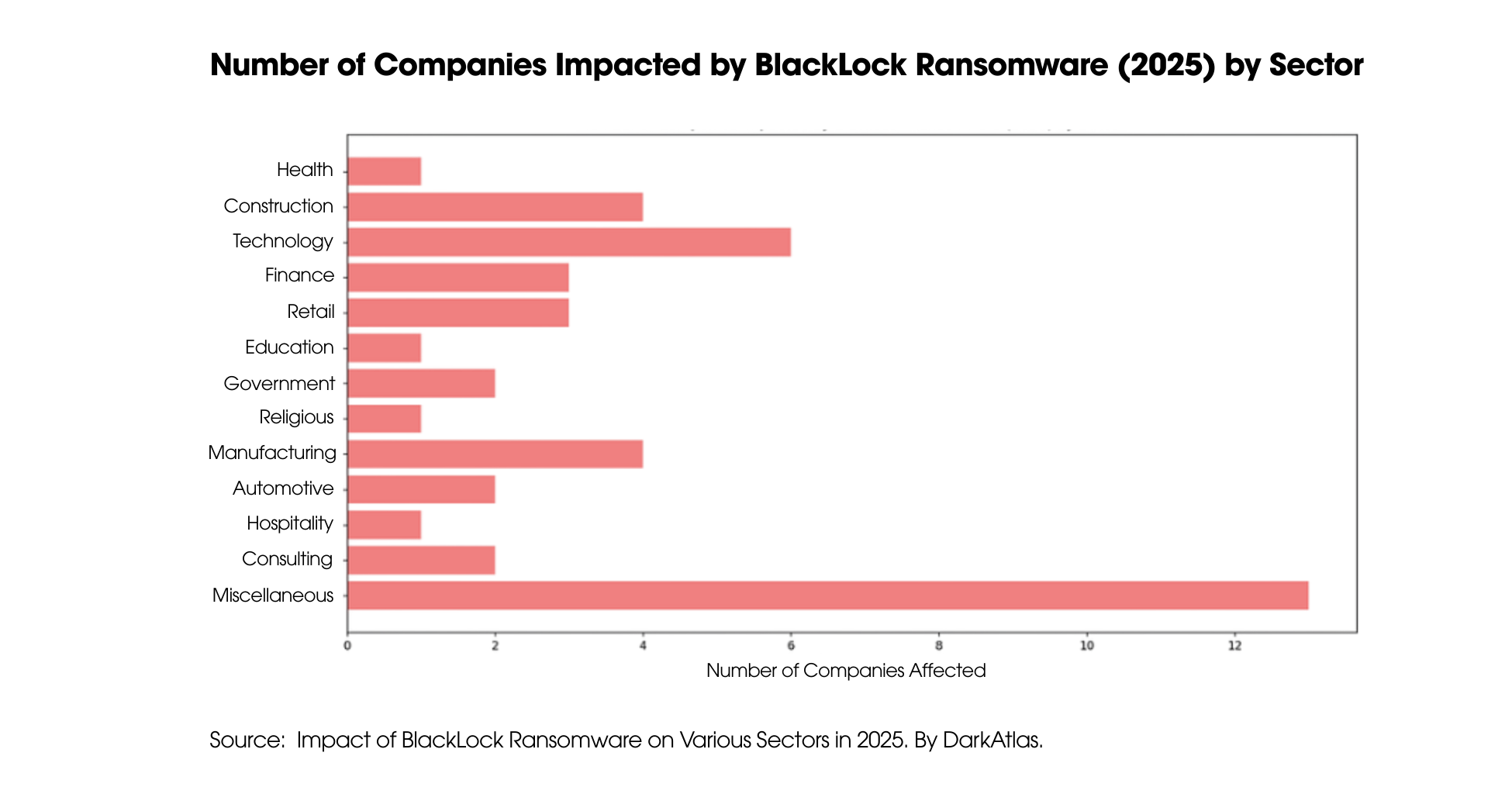
Lynx remains as a highly organized RaaS group, offering affiliates professional tools, an automated panel, and an “All-in-One” ransomware kit. Meanwhile, Medusa has expanded its use of triple extortion—encrypting data, stealing it, and manipulating victims into paying multiple times.
These groups are no longer just hackers; they are structured operations with business models, support channels, and recruitment pipelines. Their success depends on scale, speed, and stealth.
When cyber threats look harmless, awareness becomes critical
As threats multiply, so must defenses. It is no longer enough to block obvious threats. Organizations must now think like attackers. Where are users being tricked? Which trusted tools are being weaponized? What’s hiding in plain sight?
Security teams must strengthen identity controls, apply real-time monitoring, and update systems continuously. Most importantly, they must invest in awareness—because many of these attacks begin not with code, but with a click.
In 2025, the most dangerous threats are the ones that look harmless—and cybercriminals know it. Companies must stay up to date with the latest tactics, and employee training is key to keeping these actors away from the organization.
If you want to learn more about available cybersecurity solutions, assessments—or simply want to have a conversation on the topic—feel free to reach out. We’re always happy to connect.











