Halloween is approaching, and with it, tales of terror that might chill you to the bone. But for businesses today, the real nightmares aren’t in ghost stories—they’re in cybersecurity threats. With new and evolving tactics, cybercriminals can bring havoc to unprepared organizations. Let’s dive into some chilling stats highlighting the most common cybersecurity threats for businesses and explore how they can protect against these terrifying trends.
95% of Data Breaches Stem from Human Error: The Role of Human Element in Cybersecurity Threats
Human error is a common factor in cybersecurity incidents. Astonishingly, 95% of all data breaches are caused by mistakes made by individuals within an organization. A missed update, a careless click on a phishing email—these simple errors open doors for attackers. While humans are a weak link, regular training can greatly mitigate risks. Teaching employees to recognize phishing attempts and other suspicious activity helps build a stronger first line of defense.
Addressing this aspect can significantly improve cybersecurity in your organization. When people understand their role in maintaining security, they become empowered to prevent potential breaches.
The Rising Cost of Cyber Breaches
Cybersecurity threats are not just scary; they are also incredibly costly. In 2024, the average cost of a data breach in Canada reached a staggering $4.66 million USD. These costs are not just associated with lost revenue or ransom payments. They also include expenses related to recovery, legal fees, and damage to the organization’s reputation.
For businesses, ignoring cybersecurity is no longer an option. The financial impact of a breach can be devastating. Investing in cybersecurity solutions and practices to prevent these breaches is essential.
A cyberattack occurs every 39 seconds

Hackers are lurking everywhere. Cyberattacks happen every 39 seconds, and ransomware is expected to strike every 2 seconds. It’s like having an invisible intruder constantly knocking on your door, hoping for a way in. This highlights the persistence of cyber criminals and the importance of always being vigilant.
Businesses must adopt continuous monitoring to identify and respond to attacks quickly. Having a solid cybersecurity strategy in place ensures that these frequent attacks are met with strong defenses. Every organization should consider cybersecurity as an ongoing commitment, not just a one-time setup.
Small Businesses Are Big Targets
It’s a common misconception that only large companies are at risk. In reality, nearly 43% of all cyberattacks target small businesses. Why? Because they are often seen as “easy pickings” by cybercriminals. Many small businesses lack the resources to implement robust cybersecurity measures, making them vulnerable to attacks.
However, affordable solutions are available. Cloud-based security services and managed security providers offer small businesses protection that scales with their needs and budgets. For smaller organizations, it’s vital to recognize the threat and invest in appropriate safeguards.
Cloud Attacks: The Rising Threat
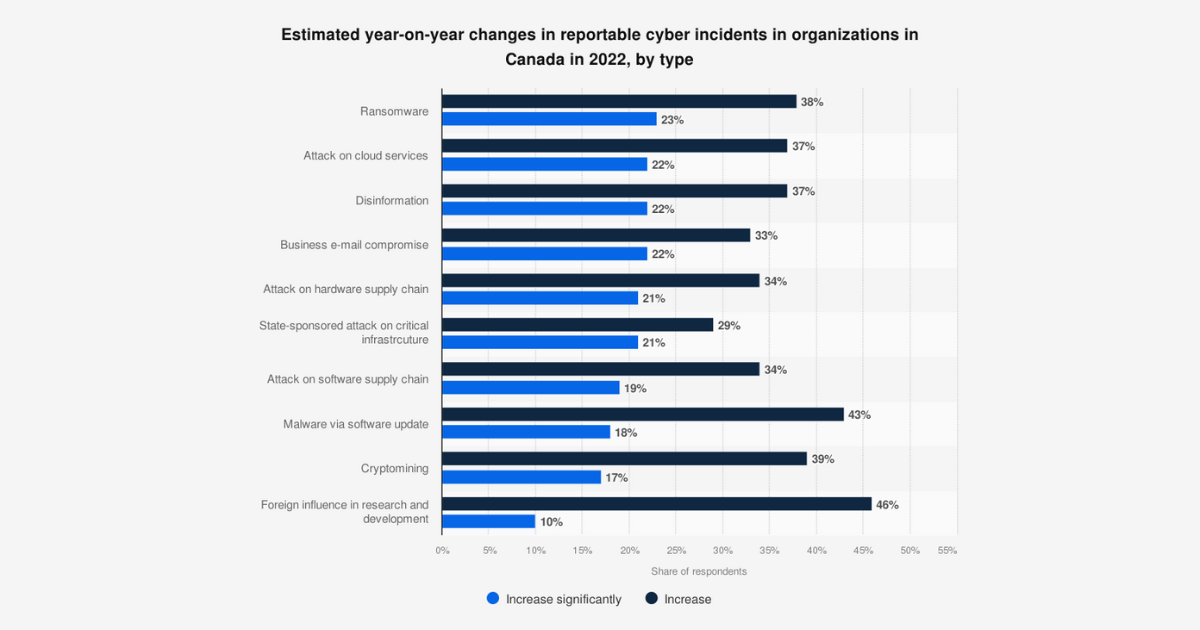
PwC © Statista 2024. Estimated year-on-year changes in reportable cyber incidents in organizations in Canada in 2022 by type.
With 83% of organizations relying on the cloud, attacks on these services are soaring. In Canada, cloud attacks are the second most common threat. As more of us rely on the cloud, it’s critical to lock down your data.
Securing cloud data is critical. Multi-factor authentication, data encryption, and access control are essential. As businesses continue to migrate data to the cloud, they must stay vigilant to ensure their data remains protected from cybercriminals.
Cybercrime Costs Keep Rising
Cybercrime costs are projected to reach $3.97 billion USD in Canada by the end of this year and $4.78 billion by 2028. These figures reveal the growing economic impact of cyber threats and the urgent need for businesses to take cybersecurity seriously.
Investing in cybersecurity may seem expensive, but the costs of neglect are far higher. As these trends continue, businesses must prioritize cybersecurity solutions that protect their data and mitigate the financial risk of breaches.
Ransomware attack on the Rise
Ransomware continues to be one of the most common cybersecurity threats for businesses. In Canada, 38% of cyber incidents are ransomware-related, and the average cost per data breach stands at $4.54 million USD. Ransomware attacks don’t just demand money—they also disrupt operations, damage reputation, and cause long-term harm.
Developing a ransomware response plan is crucial. Businesses should focus on both prevention and recovery. Implementing strong backup procedures and anti-ransomware tools can help mitigate the impact of an attack. In the event of a breach, having a well-prepared response strategy can make the difference between a quick recovery and prolonged downtime.
The Nightmare of Repeat Breaches
Cybersecurity is not a one-and-done deal. Shockingly, 83% of organizations have experienced more than one breach. This statistic underscores the need for continuous vigilance and adaptation. Cybercriminals are constantly evolving their tactics, and organizations must keep up.
Regularly updating software, patching vulnerabilities, and conducting security assessments are essential practices for preventing repeat breaches. A proactive approach, combined with regular audits, helps ensure that businesses stay one step ahead of potential threats.
Phishing: The Cybercriminal’s Favorite Trick
Phishing remains a pervasive threat. An estimated 91% of data breaches in 2024 are linked to phishing. Cybercriminals craft fake emails, often mimicking trusted brands or colleagues, to lure unsuspecting victims. It takes just one click to compromise an entire organization.
Regular phishing awareness training is crucial for all employees. Encouraging a “think before you click” mindset can help prevent these attacks. Phishing may be one of the oldest tricks in the book, but it remains highly effective. Businesses that invest in training and email security tools are better equipped to defend against it.
A Call to Action: Fighting Cybersecurity in 2024
These cybersecurity trends and statistics may be scary, but they serve as a powerful call to action. For businesses, staying informed is the first step to staying secure. It’s important to be proactive and implement strategies that address the most common cybersecurity threats for businesses.
As businesses face increasingly complex cybersecurity threats, it’s vital to take proactive measures to stay protected. From human error to the rising costs of breaches, no organization is exempt from these risks. Protecting your business requires adopting robust security practices. At Cloud Managed Networks, we specialize in helping businesses navigate these threats with tailored cybersecurity solutions that provide peace of mind. Don’t let cyber threats haunt your business—reach out to our team to explore how we can help safeguard your business against evolving threats.











