- News & Resources: Listings >
- Blog
- How OCWA modernized water infrastructure with Cisco industrial IoT
- Redefining physical security in healthcare: A response to rising violence
- Emerging Cyber Threats in 2025: Tactics Redefining Digital Risk
- The Three Shields: How Firewalls Defend Modern Enterprises
- Workplace Safety in Crisis: Protecting Frontline Workers from Rising Threats
- The Role of Industrial Networking in Modern Manufacturing
- Why Cybersecurity for SMBs Must Be a Top Priority in 2025
- Together We Give: CMN and Umbrella’s Commitment to Support our Community
- The State of Shoplifting report reveals that 24% of shoppers switch stores due to shoplifting.
- How to Improve Safety and Security in Schools – Cloud Manage Network
- Top 10 Cybersecurity Threats in 2024
- Microsegmentation: Protecting Data from Cyber Threats
- Retail shoplifting and loss prevention: How to protect your business
- Generative AI Cost Optimization Strategies
- Why Do I Need to Protect My Cloud?
- 10 Reasons for Engaging Outside Experts to Manage Your Cybersecurity
- Why Hiring a 3rd Party MSP Expert Makes Sense and – and Cents (MANY cents!)
- Brand and Network Considerations When Adopting AI Corporately
- Integrating XDR, SIEM, and SOAR
- 3-2-1 –Go? Not so quick, this time.
- 5 Things a CISO Shoud Know
- 10-Step Patch Management Checklist
- Penetration Testing vs. Breach Attack Simulation
- Current big cyber breaches and impact on businesses
- Smart Infrastructure Gets Lit Up!
- Securing Industrial IoT: The Missing Puzzle Piece
- 7 Common Cybersecurity Mistakes Made by SMBs
- The Future of Physical Security: Cloud-Based Systems
- Autonomous and Sensor Technology Use Surging
- 2024 Facilities Trends Will Require Facilities and IT Teams to Work in Tandem
- NGFW vs. WAF. What’s the Right Firewall for You?
- Chris Hadfield’s Words To Live By
- Industrial Revolution 4.0 + IIoT
- Digital Fluency Drives Innovation
- Your Cloud Needs Protecting, Too
- Your building alarm systems could become obsolete. In 2024!
- Zero Trust 2.0: Zero Trust Data Resilience (ZTDR)
- We just got, or got used to, Wi-Fi 6. What is Wi-Fi 7?
- What Does the Board Need to Know? Business Metrics that CISOs Should Share – 4th and Last in a Four-Part Series
- Why 2024 is the Year for AI Networking
- International Women’s Day is Tomorrow – Great Time to Think About…
- Data-Centric Security Step One: Classifying Your Data
- The Network – Unsung Hero of Super Bowl LVIII
- What Does the Board Need to Know? Business Metrics that CISOs Should Share – Third in a Four-Part Series
- Boosting IT Team Performance by Fostering Intuition, Curiosity and Creativity
- Breach Remediation Costs Can Wipeout Bottom Line and Business
- Hoodied Hackers Now Favour Hugo Boss
- What Do You Need to Tell the Board? Business Metrics that CISOs Should Share – Second in a Four-Part Series
- How to Get People to Re-Engage After the Holidays
- What Does the Board Need to Know? Business Metrics that CISOs Should Share – First in a Four-Part Series
- Android Devices MUST be Updated + IT Departments Being Cut as Privilege Escalation Escalates
- Today’s Common Cloud Migration and Management Concerns
- Protect Your Healthcare Network from Cyberattack – Lives are at Stake
- Happy Halloween: Black Cats Lead to Boo….Hoo.
- Insurance Underwriters are Protecting Their Flanks
- Insurance Companies Cracking Down as Cybercriminals Become Better Business Builders
- Scary Cyberattacks Stats
- Parents, Profs and IT Professionals Perceive Back-to-School Through Different Lens
- Zscaler’s new IDTR and other tools that leverage generative AI
- Vanquish Vaping, Vandalism and Villainy
- Fabric for Fast-Paced Environments
- Changes to Cyber Insurance Requirements – What you Need to Know
- Cybersecurity Readiness – Newly Released Report
- Passwords Leaked…Again
- 10-Step Patch Management Checklist
- Remote – Again – For Now… and Still Maintaining Engagement
- Protecting Pocketbooks, Passwords and Property from Pilfering
- Raspberry Robin: Highly Evasive Worm Spreads over External Disks
- Cisco Introduces Responsible AI – Enhancing Technology, Transparency and Customer Trust
- Managing Customer Trust in Uncertain Supply Chain Conditions
- Hope on the Horizon
- Toys of Tomorrow… What will spark your imagination? Fuel your imagination?
- Protecting Purses and Digital Wallets
- The Password that Felled the Kingdom + MFA vs 2FA
- The MOE’s RA 3.0 and Zscaler
- 7 Critical Reasons for MS Office 365 Backup
- Penetration Testing Important, but…
- Social Engineering and Poor Patching Responsible for Over 90% of Cybersecurity Problems
- Breach Incidence and Costs On the Rise Again + 5 Ways to Reduce Your Risk
- Cybersecurity Insurance Policies Require Security Audits and Pen Testing
- Wireless strategies for business continuity gain importance as enterprise expand IoT, cloud, and other technologies
- How Cybercrooks are Targeting YOU
- Enabling Digital Transformation with Cisco SD-WAN
- WFH Post Pandemic – What It Will Look Like. What You’ll Need.
- Leaders to looking to the IoT to improve efficiency and resiliency
- Cyber Security Vernacular – Well, some of it, for now
- Why You Need Disaster Recovery, NOT Just Back-Ups
- 10 Reasons Why Having an Expert Manage Your Cybersecurity Makes Sense and Saves Dollars
- Converting CapEx IT Investments into Manageable OpEx
- The Hybrid Workplace – Planning the Next Phase
- Cisco Cloud Calling: Empowering Customers to Thrive with Hybrid Work
- When You Can’t Access the Cloud
- How to Keep On Keeping On
- New Cisco Research Reveals Collaboration, Cloud and Security are IT’s Top Challenges
- Threats from Within on the Rise
- Cloud Covered? If Not, Take Cover!
- Zero Trust and Forrester Wave Report
- Password Based Cyber Attack: Like Leaving Keys Under Doormats
- So, What’s Up With Sensors?
- Sensors and Systems Create a Digital “Last Mile” and Help Skyrocketing Costs
- Scanners Provide Peace of Mind for Returning Students and Workers
- Sensors Improve Operations and Bottom Line… Easily and Cost-Affordably.
- Cisco Meraki Looks at 2021
- 2020 Holiday Shopping: Cybersecurity and Other Tips to Safeguard Wallets and Systems
- How to make the most of the technology you have
- Personnel, Planet and Business Progress: More Interdependent Than Ever Before
- Sure… you can get them all in the boat – but can you get them to work well together?
- Pushing the Zero Trust Envelope – Cisco is Named a Leader in the 2020 Forrester Zero Trust Wave
- Cloud Data Must be Protected, Too!
- Don’t Let Anyone Get the Dirt on You – Make It Instead!
- How IoT Devices Can Help You and Your business
- WebEx – A World of Possibility
- Creating Your Breach Response Plan Now Will Save You Thousands Down The Road
- Been hacked? Here’s what you must do next.
- The Need for Pen Testing is At an All-Time High
- 5 Ways an IT Reseller Improves Your Performance and Peace-of-Mind
- 5G and Wi-Fi 6: Faster, more flexible, and future ready. Are you?
- Network and Data Security for Returning and Remote Workers + Disaster Recovery Symposium
- Collaboration and Cisco WebEx: Protecting Your Data
- Thursday’s Virtual Conference Tackles Today’s Supply Chain Trials and Tribulations
- 10 Tips to Reduce Cloud Storage Risk
- COVID-19 Crisis Fuelling IT Spending
- Supply Chain/Logistics Experts Share Their Expertise
- Cisco Breach Defence Overview
- Announcing Our New Website and Blog
 In healthcare today, ensuring the physical safety of both staff and patients is not just a function of daily operations—it is a foundational responsibility that directly impacts the quality and continuity of care. The alarming rise in workplace violence has created an urgent need for more cohesive and intelligent security frameworks. While digital innovation has advanced clinical care, physical security in many healthcare settings remains outdated, fragmented, and insufficient.
In healthcare today, ensuring the physical safety of both staff and patients is not just a function of daily operations—it is a foundational responsibility that directly impacts the quality and continuity of care. The alarming rise in workplace violence has created an urgent need for more cohesive and intelligent security frameworks. While digital innovation has advanced clinical care, physical security in many healthcare settings remains outdated, fragmented, and insufficient.
Understanding the risk of lacking physical security in the healthcare workplace
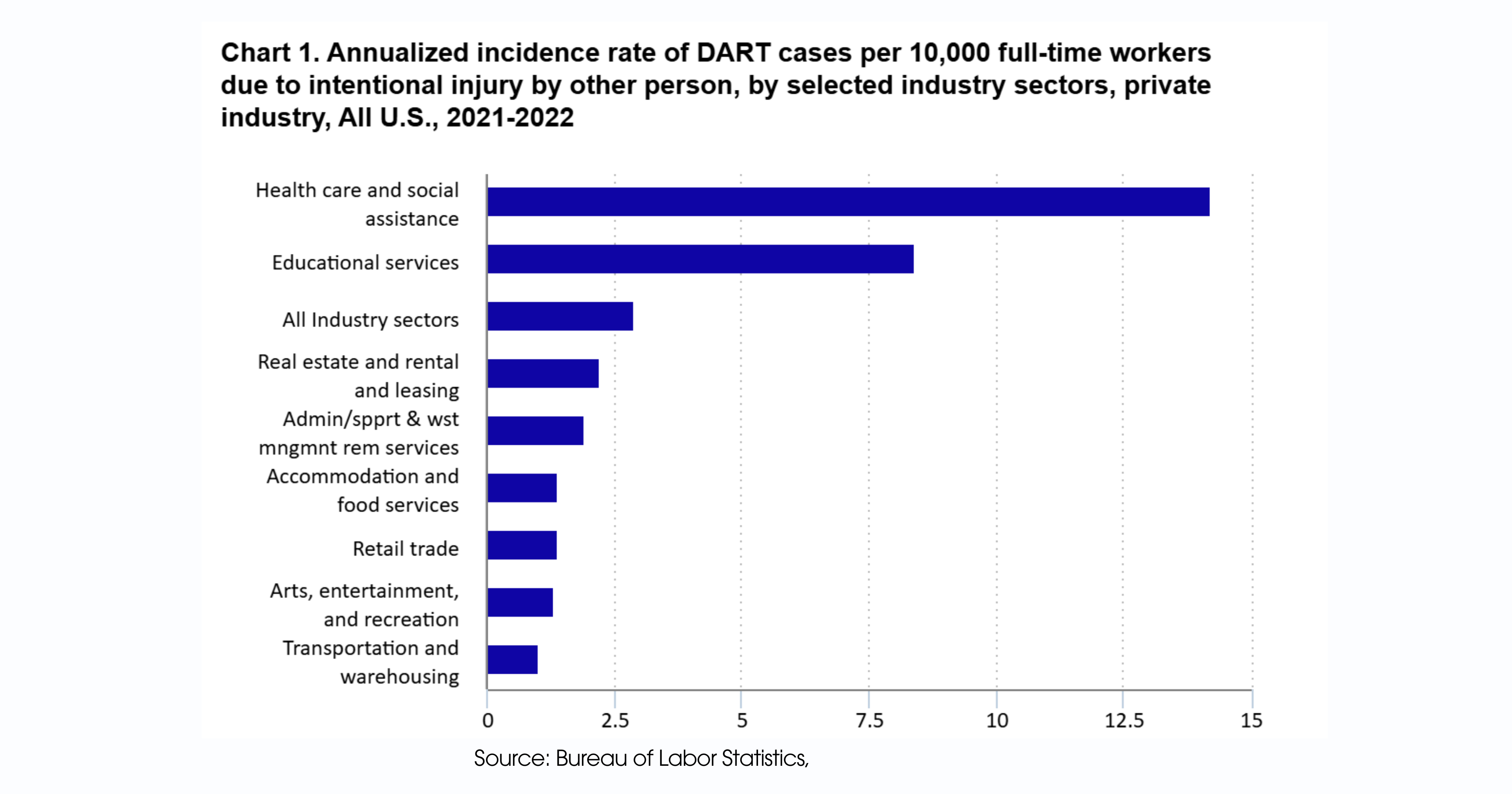
The healthcare sector is facing a silent epidemic—workplace violence. According to the Bureau of Labor Statistics, the healthcare and social assistance sectors accounted for 73% of all workplace violence incidents requiring days away from work in 2021–2022. These incidents occurred at a rate of 14.2 per 10,000 full-time workers, compared to just 2.9 across all private industries.
Healthcare workers are now five times more likely to experience violence on the job than those in other sectors. This includes everything from verbal abuse to physical attacks, with emergency departments, psychiatric units, and long-term care facilities often the most affected.
A 2022 survey by National Nurses United painted a stark picture:
- 81.6% of nurses experienced at least one form of workplace violence.
- 45.5% reported an increase in violence on their unit.
- Common experiences included verbal threats (67.8%), physical threats (38.7%), and scratches or pinches (37.3%).

These alarming numbers highlight a breakdown in physical safety measures and a growing need for comprehensive solutions.
The cost of inaction: beyond the physical harm
Security lapses in healthcare settings lead to far-reaching consequences. Not only do they jeopardize staff and patient well-being, but they also expose facilities to financial, legal, and reputational risks. Incidents can trigger lawsuits, insurance claims, regulatory fines, and loss of public trust.
Moreover, the psychological toll on healthcare professionals contributes to burnout, absenteeism, and high staff turnover. In an industry already battling talent shortages, maintaining a safe work environment is not optional—it’s a necessity.
Security challenges require modern solutions
Today’s security threats are multifaceted, requiring healthcare organizations to move beyond siloed safety protocols. Traditional surveillance and manual access logs are no longer sufficient. Instead, integrated security solutions provide the visibility, coordination, and intelligence needed to prevent incidents and respond quickly.
What is an integrated security solution?
An integrated security solution brings all these components into one unified platform. It connects door access systems with surveillance cameras, air quality sensors, visitor management, and panic buttons. Security staff can monitor activity, verify incidents, and initiate response actions—often in seconds rather than hours.
This unification also enables:
- Real-time monitoring across multiple sites
- Instant alerts and forensic search capabilities
- Seamless coordination among security, IT, and clinical teams
This unified approach to physical security improves situational awareness, reduces incident resolution times, and supports a safer environment. These systems bridge the communication gap across devices and sites, delivering full context and addressing critical visibility challenges. For healthcare providers, this shift is not just about adopting technology—it’s about fostering a workplace where safety forms the foundation of care delivery.
Unified security in action: Transforming safety and compliance at El Centro Regional Medical Center
A real-world example of how unified security systems enhance safety, compliance, and operational efficiency can be seen at El Centro Regional Medical Center (ECRMC). Located near the U.S.-Mexico border, ECRMC serves a diverse population and operates within strict regulatory standards.
With security oversight from Emergency Preparedness Director William DuBois, the hospital deployed hybrid cloud cameras, air quality sensors, panic buttons, and mobile monitoring apps. The results were profound:
- 83% reduction in workplace violence, from over a dozen incidents monthly to just 1–2.
- Investigation times reduced from several hours to 15 minutes.
- Significant regulatory cost avoidance, including potential fines starting at $25,000.
Security personnel can now stream up to 300 camera feeds in real time and coordinate responses through a mobile command application. Panic buttons discreetly protect staff in vulnerable areas, and facial blurring helps maintain patient privacy while complying with HIPAA.
Scaling smart: How PHNTX unified security across 13+ locations
Another compelling example of unified security in action is Prism Health North Texas (PHNTX), the largest nonprofit HIV care provider in the region, illustrates this transformation. With more than 13 locations, they faced growing challenges with siloed security systems. Cameras, access controls, and monitoring devices operated independently, making it difficult to respond to incidents or scale operations.
According to Infrastructure Director Matthew Shaw, the decision to deploy a fully integrated solution helped them streamline operations and improve overall safety. The system was intuitive and scalable, offering plug-and-play deployment, easy learning curves for new staff, and centralized management.
Key features included after-hours intrusion detection with real-time video verification, environmental sensors for compliance-sensitive areas, and immediate alerting through text and email. “Within seconds, I can determine the cause and share the footage with first responders,” Shaw explained.
Five ways to improve physical security in healthcare facilities
To effectively address the growing threat of workplace violence and ensure the safety of staff and patients, healthcare organizations must take decisive action. Here are five proven strategies to elevate security in any healthcare setting:
- Adopt Cloud-Managed Surveillance with AI: Invest in cameras that offer real-time alerts, motion detection, and facial recognition. AI-powered systems can detect when patients exit their rooms unsupervised or when suspicious movement occurs in sensitive zones like pharmacies or ICUs. These systems offer 24/7 recording with minimal bandwidth usage and can store up to 365 days of footage, ideal for investigations or audits.
- Control Access to Sensitive Areas: Limit entry to high-risk zones such as surgical suites, maternity wards, and psychiatric units through access-controlled doors. Pairing these doors with security cameras adds an extra layer of context to any access event, such as tailgating or forced entry.
- Implement Advanced Visitor Management: Modern visitor management systems use photo ID capture, badge printing, and integration with electronic medical records (EMRs). They screen guests against watchlists and patient-specific restrictions, ensuring that only approved individuals gain access to care areas. Front desk staff can also monitor visitor volumes in real time and enforce safety policies efficiently.
- Train Staff on De-escalation and Emergency Protocols: Conduct regular training on recognizing early signs of aggression, de-escalation techniques, lockdown and emergency response drills. Preparedness saves lives and builds a culture of accountability and safety.
- Use Data Analytics for Proactive Threat Detection: Modern platforms like Verkada allow organizations to analyze trends across time and locations. This enables early detection of high-risk zones or frequent offenders, allowing for proactive policy changes. Alerts can be configured based on custom parameters, including entry at odd hours, repeated access attempts, or lingering in restricted areas.
Building a Safer Future in Healthcare
Healthcare professionals should not have to fear for their safety while providing essential care. The rise in workplace violence underscores the need for advanced, responsive, and unified security systems that adapt as organizations grow.
The experiences of PHNTX and ECRMC reveal the tangible benefits of a well-integrated, cloud-based platform. Not only are these organizations meeting safety goals, but they are also enhancing compliance, improving operational efficiency, and restoring confidence across staff and patient communities.
Physical security is no longer a support function. It’s foundational to care delivery and healthcare excellence. At Cloud Managed Networks, we bring extensive experience in helping healthcare organizations create safer, more resilient workplace environments. If you have questions or would like to start a conversation, we’d be glad to connect.