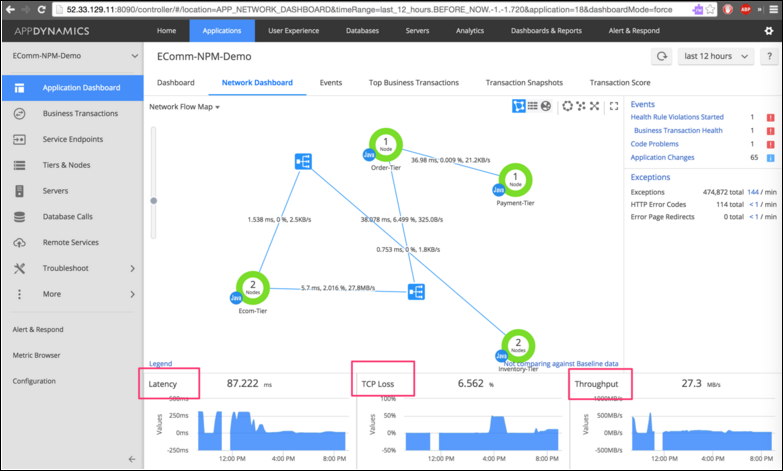
We work with all top manufacturers and have IT experts on staff, so we can recommend the best solution for your situation, building on whatever you currently have in place.
In short, from hardware to software, on-premise and in the cloud… You need it? We’ve got it. Not sure what you need? We can help.